Why is WordPress Security so Important?
WordPress powers over 32% of all websites on the internet, and it is becoming a huge target for hackers, DDOS and other malicious attacks. With thousands of themes and plugins out there, it’s not surprising that vulnerabilities exist and are being discovered on a daily basis. As a WordPress website owner, it is your responsibility to make sure that your website does not have any security flaws which could be exploited.
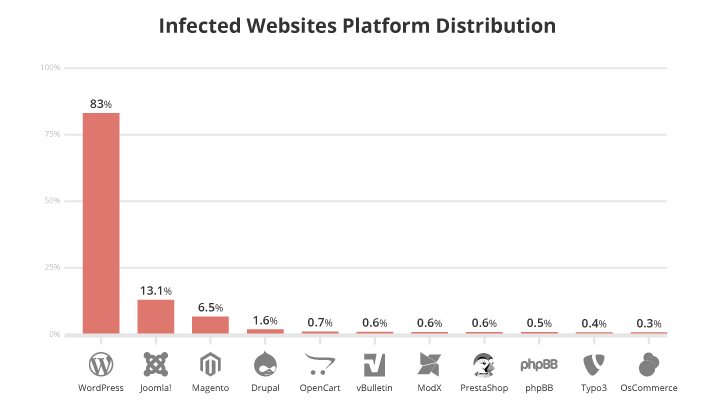
Below is a side by side comparison of the most popular Content Management Systems.
As you can see WordPress is by far the number one infected platform. This does not mean that WordPress is not secure. In fact, the core WordPress files are extremely secure. Most of these Infections are due to poorly coded plugins and themes.
A hacked WordPress site can cause serious damage to your business revenue and reputation. Hackers can steal information, passwords, install malicious software, and can even distribute malware to your visitors. When it comes to security, there are a lot of things you can do. So in this guide, we are going to be sharing our best tips, strategies, and techniques that you can use to secure your WordPress website.
Table of Contents
- Find Good WordPress Hosting
- Get a Secure WordPress Theme
- Remove Unused Plugins & Themes
- Keep WordPress Up to Date
- Backup, Backup, Backup!
- Disable File Editing
- Remove WordPress Version
- Disable Directory Browsing
- Protect Sensitive Files
- Limit Login Access
- Limit Admin Panel Access
- Protect Against SQL Injection
- Change the Default Database Prefix
- Disable XML-RPC
- Our Recommended Security Plugins
- My Final Thoughts
Find Good WordPress Hosting
When it comes to WordPress security, there is much more than just locking down your website. There is also web server security for which your WordPress host is responsible.
Using WordPress hosting provides a more secure platform for your website. Unlike normal shared hosting, WordPress hosting is a hosting environment that’s specifically designed to cater to WordPress websites. Every aspect of the server is set up with WordPress reliability, speed, security and ease-of-use in mind.
Three important things to look for in a good WordPress host are:
- Automatic WordPress Updates
- Automatic WordPress Backups
- WordPress Specific Security
Here at Zuziko, I use Hostgator WordPress Cloud Hosting. I have been using Hostgator for about three years now, and I am very happy with the service. WpEngine and Liquid Web are worth checking out as well.
Get a Secure WordPress Theme
A secure WordPress theme is one that doesn’t include any known security vulnerabilities, is consistently updated, follows proper code standards, and is compatible with both your version of WordPress and your site’s other elements such as plugins.
Having a theme that meets all these criteria will help you avoid unnecessary bugs, compatibility errors, and similar issues. You’ll also make it a lot harder for hackers, malware, and other undesirable influences to impact your website because there will be fewer security holes for them to exploit.
You can always check if your theme is secure using the tools we’ll discuss in a moment. However, the best way to find a safe theme is to get it from a reputable source. Below are a few themes that I use myself and highly recommend:
If you already have a WordPress theme you can use a plugin such as Theme Check. The theme check plugin is an easy way to test your theme and make sure it’s up to spec with the latest WordPress theme standards. A passing score doesn’t necessarily mean your theme is perfect, but it is an indicator of solid coding practices.
Remove Unused Plugins and Themes
When you are creating your WordPress website you will most likely be testing out several plugins and themes before you decide on your final ones. Make sure to remove any that you are not going to be using on the live website.
Even though a theme or plugin is not enabled and active it can still open up security holes for hackers to get in. This is because the plugin or theme files that could potentially be a security risk are still located in your /wp-content/ directory.
Keep WordPress Up to Date
Almost every WordPress website that is not kept up to date will be hacked sooner or later. Hackers use scripts that search the internet specifically for outdated and vulnerable WordPress plugins and themes.
For this reason, it’s extremely important to keep your plugins, themes, and core WordPress files up to date. In fact, this might be one of the most important things you can do in this whole guide.
Most of the time you can do WordPress updates from the Dashboard > Updates. However, if you have purchased premium plugins or themes you may have to go directly to their website to download the latest version.
Make sure to get a backup of your website files and database before you update. Sometimes updating to a newer version of WordPress can break your website especially if you are using plugins and themes that are outdated.
Backup, Backup, Backup!
Keeping a current backup of your website is crucial. This is not only important for security reasons but is just a good idea in general. Having a backup of your website allows you to quickly restore your WordPress site in case anything were to happen.
Depending on how often you edit your website, you may want to update weekly or even daily. I personally get a backup anytime I make changes big or small. You can manually backup your WordPress website (this is what I do) or you can use one of the many backup plugins available. UpdraftPlus and BackWPup are two of the most popular and offer a ton of features.
Related: Our pick for Best WordPress Backup Plugin
Disable File Editing in the Dashboard
By default, WordPress allows admins to edit the theme and plugin code through the dashboard. While it is a great feature, it can be a security risk especially if you have multiple users.
If you have multiple users that login to your WordPress dashboard, it’s important to assign the correct role to each user. Only allowing access to the things that are necessary. If you happen to forget or make a mistake when assigning roles it could give someone access to your file editor.
A single typo in one of these files can completely break your website. The file editor is also an easy way for a hacker to run malicious code. For these reasons, I recommend that you disable it completely.
You can disable this feature completely by adding the following code to your wp-config.php:
define('DISALLOW_FILE_EDIT', true);Remove WordPress Version
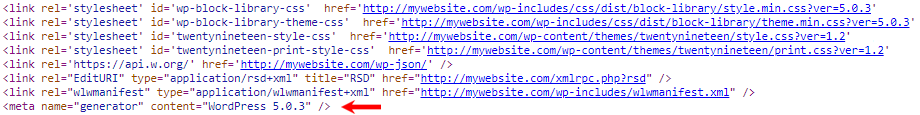
By default, WordPress displays its version info in your source code. This is used for tracking purposes and can be a big security risk. Hackers can use this information to exploit known vulnerabilities on a particular version. For this reason, it’s a good idea to remove the version number from all areas of your website.
To remove the WordPress version number from all areas of your website, add the code below to your theme’s functions.php:
// remove version from head
remove_action('wp_head', 'wp_generator');
// remove version from RSS
add_filter('the_generator', '__return_empty_string');
// remove version from scripts and styles
function shapeSpace_remove_version_scripts_styles($src) {
if (strpos($src, 'ver=')) {
$src = remove_query_arg('ver', $src);
}
return $src;
}
add_filter('style_loader_src', 'shapeSpace_remove_version_scripts_styles', 9999);
add_filter('script_loader_src', 'shapeSpace_remove_version_scripts_styles', 9999);
If you always use the latest version of WordPress this is not as big of a deal. However, I still remove my WordPress version because I want to give out as little information as possible to a potential hacker.
Disable Directory Browsing
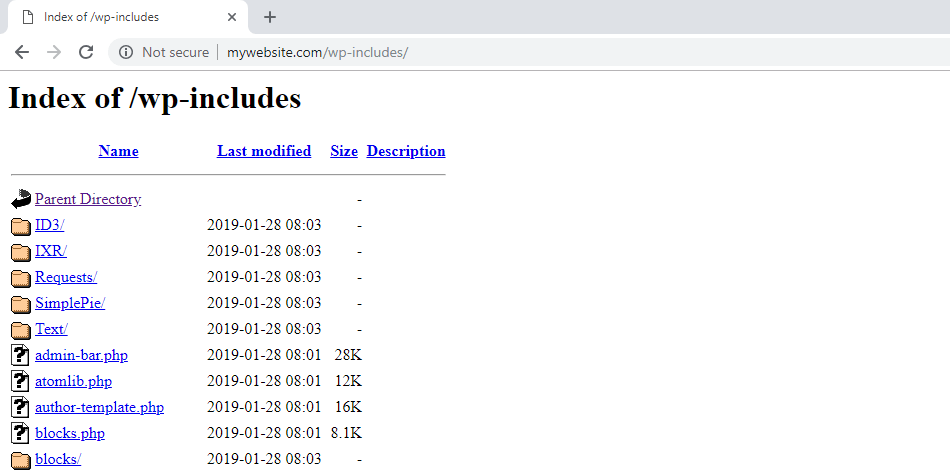
Have you ever visited a webpage and noticed a listing of files instead of the actual HTML similar to the picture below? Servers will display the directory listing in the absence of an index page. What this means is that if a visitor types the path of a certain directory such as https://zuziko.com/wp-includes/ and there is no index.php file, the server will display everything inside this folder. This can be dangerous, as it gives a hacker the ability to explore the inner workings of your website.
The good news is that this can easily be prevented by adding a single line of code to your .htaccess file. To disable directory browsing open your .htaccess file and paste the following code inside:
# Disable directory browsing
Options All -Indexes
Protect Sensitive Files with .htaccess
A WordPress installation contains sensitive files, such as the wp-config.php, license.txt, and readme.html files. It’s best to keep these files hidden from outside access as they contain sensitive information.
Some of these files can be deleted. However, they will be back again when you update to a newer version of WordPress. For this reason, it’s best to just hide them using your .htaccess file. That way you don’t have to worry about it anymore.
Copy and paste the code below into your .htaccess file located in the root directory:
# Protect .htaccess
<files .htaccess>
Order allow,deny
Deny from all
</files>
# Protect readme.html
<files readme.html>
Order allow,deny
Deny from all
</files>
# Protect license.txt
<files license.txt>
Order allow,deny
Deny from all
</files>
# Protect wo-config.php
<files wp-config.php>
Order allow,deny
Deny from all
</files>
# Protect error_log
<files error_log>
Order allow,deny
Deny from all
</files>
Limit Login Access
A Brute Force Attack is one of the more common ways to gain access to a website. By default, WordPress will allow users to enter usernames and passwords as many times as they want. Hackers use programs that try usernames and passwords, over and over again, until they get in or the server dies. A common attack point on WordPress is the wp-login.php.
There is an easy way you can fix this problem. Open your .htaccess file and paste the code below inside. Replace xx.xx.xx.xx with your external IP and anyone else’s IP that will need access to login. You can find your IP at https://www.whatismyip.com.
# Limit Login Attempts
<Files wp-login.php>
order deny,allow
Deny from all
allow from xx.xx.xx.xx
allow from xx.xx.xx.xx
</Files>
This will prevent everyone (except the IP’s you specify) from accessing the wp-login.php page.
Limit Access to WordPress Admin Panel
The same way we blocked wp-login.php above we can also block the Dashboard area of WordPress. If you are the only person who needs to login to your Admin area, you can deny wp-admin access to everyone but yourself using an .htaccess file. For this, we will need to create a new .htaccess file inside of your wp-admin folder.
Create a new file inside your wp-admin folder named .htaccess and add the following code:
# Block access to wp-admin
order deny,allow
allow from xx.xx.xx.xx
allow from xx.xx.xx.xx
deny from all
Replace xx.xx.xx.xx with your external IP address and anyone else’s IP that will need access to the WordPress Dashboard.
If your theme or plugins use AJAX, you will most likely need to add an additional group of settings to your .htaccess so that functionality continues to work:
# Allow access to admin-ajax.php
<Files admin-ajax.php>
Order allow,deny
Allow from all
Satisfy any
</Files>
This will prevent everyone (except the IP’s you specify) from accessing the WordPress dashboard.
Protect against SQL Injection
SQL Injection is the most commonly used hacking technique to manipulate WordPress databases. SQL injection attacks occur when a web application does not validate values received from a web form, cookie, input parameter, etc.
An attacker can easily abuse the input fields by inserting malicious code that can execute SQL commands. These commands can create, retrieve, update, and even delete the data in your WordPress database.
Below I have shared some code that can be inserted into your website’s .htaccess file. This code will lay down a strong set of rules to help protect you from many serious SQL injection attacks.
# Protect Against SQL Injection
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteCond %{REQUEST_METHOD} ^(HEAD|TRACE|DELETE|TRACK) [NC]
RewriteRule ^(.*)$ - [F,L]
RewriteCond %{QUERY_STRING} \.\.\/ [NC,OR]
RewriteCond %{QUERY_STRING} boot\.ini [NC,OR]
RewriteCond %{QUERY_STRING} tag\= [NC,OR]
RewriteCond %{QUERY_STRING} ftp\: [NC,OR]
RewriteCond %{QUERY_STRING} http\: [NC,OR]
RewriteCond %{QUERY_STRING} https\: [NC,OR]
RewriteCond %{QUERY_STRING} (\<|%3C).*script.*(\>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} mosConfig_[a-zA-Z_]{1,21}(=|%3D) [NC,OR]
RewriteCond %{QUERY_STRING} base64_encode.*\(.*\) [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(\[|\]|\(|\)|<|>|ê|"|;|\?|\*|=$).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*("|'|<|>|\|{||).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(%24&x).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(%0|%A|%B|%C|%D|%E|%F|127\.0).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(globals|encode|localhost|loopback).* [NC,OR]
RewriteCond %{QUERY_STRING} ^.*(request|select|insert|union|declare).* [NC]
RewriteCond %{HTTP_COOKIE} !^.*WordPress_logged_in_.*$
RewriteRule ^(.*)$ - [F,L]
</IfModule>
Change the WordPress Database Prefix
Your WordPress database contains sensitive information such as usernames, passwords, emails etc. This is why it’s a popular target for hackers. Hackers develop SQL injections, automated scripts, and other malicious code to attack your database and break into your website. For this reason, it’s very important that you protect your database.
Although there is no security measure that is guaranteed to be foolproof, you can still protect your website’s database from novice attackers simply by changing its default table prefix. Changing the default table prefix of wp_ to something else will make it much harder for an attacker to guess.
You can change the default database prefix by following our tutorial: How to Change the Default WordPress Database Prefix.
Disable XML-RPC in WordPress
XML-RPC is a feature of WordPress that enables data to be transmitted with HTTP acting as the transport mechanism and XML as the encoding mechanism. Since WordPress isn’t a self-enclosed system and occasionally needs to communicate with other systems, this was created to handle that job.
The biggest issues with XML-RPC are the security concerns that arise. The issues aren’t with XML-RPC directly, but instead how the file can be used to enable a brute force attack on your site. Hackers can effectively use a single command to test hundreds of different passwords. This allows them to bypass security tools that typically detect and block brute force attacks.
Sure, you can protect yourself with incredibly strong passwords, and WordPress security plugins. But, the best way to protect yourself is to simply disable it.
Copy and paste the code below into your .htaccess file located in the root directory:
# Block WordPress xmlrpc.php
<Files xmlrpc.php>
order deny,allow
deny from all
</Files>
Our Recommended Security Plugins
Investing in a solid security plugin like the ones listed below will let you scan your website for vulnerabilities, monitor actions, provide a WAF or “Web Application Firewall”, and alert you through email when something is not right. This will help harden your WordPress website even more.
Not to mention, all of these plugins will do everything I have written about in this guide (and much more) in just a few clicks.
Sucuri Security
iThemes Security (Better WP Security)
All In One WP Security & Firewall
Wordfence Security
My Final Thoughts
Hopefully, this guide has helped you learn a little bit about WordPress Security and has given you some ideas about how you can better protect your Website. If you have any questions or see anything that I can add, let me know in the comments below.